
Protection of corporate assets has always been an integral part of business. Disruption of how the convenience of communication and data availability are reminded. Network administrators know Nimda, Loveletter, SQL Slammer and others as weapons of terror for lower operators. Viruses, Trojans and other malicious code run rampant in an unprotected workplace. Damaged data, inefficient operations and damaged business reputation is the result.
The threat of business disruption, especially for operations are seriously taken by
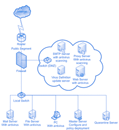
Open Technology, which can have easily customizable solutions to fit every need. From operating system coverage to message system screening and isolated redirection; Web Server lockdown to registry restricted access; Centralized Quarantine to automatic updates;
Open Technology has many important parts as scales from client to server, operating system to application, core to perimeter in dealing with virus threats.
Symantec, McAfee, TrendMicro, PANDA, NOD32 and others are the examples of skilled professionals in several vendor categories. From small office desktop coverage to Enterprise Central Nervous Systems throughout Thailand is the range of customer solutions.
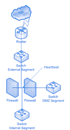
Open Technology enterprise Internet Security Solutions are designed for organizations with 100 -1,000 employees and utilize the Internet for mission critical applications to conduct daily business.
Every businesses survival which depend upon the capability, flexibility and reliability of internal communications network and secure connectivity to the WAN and the Internet are recognized by
Open Technology. Confidential e-mails, legal documents, proprietary product information and other critical documents are examples of documents which are available on the LAN but must be secured from the outside world.
The security necessary to protect assets is firewall which will insert at the front end of the LAN. Access lists and other methods such as packet filtering, Stateful Inspection, Network Address Translation (NAT) and Protection against Denial of Service (DoS) are used by a firewall router to ensure the security of the private network.
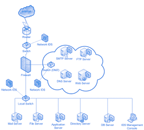
Rushing to provide valuable corporate assets via extranets and public interfacing business systems by companies, increasing exposure to threats is needed. Sensitive data becomes vulnerable to structured intercessions by interlopers and services can be disrupted by organized logical attacks.
Reaching a turning point in the intrusion detection market by consumers is the belief of Open Technology.
A clear problem is evident today is when security is too hard to use; it is often misused, degraded or not used. An analogy would be a home security system that is so complex that the family pet continually sets off the motion detectors and nobody can figure out how to respond.
It won't be used if the system is overwhelming. The value for cost is not realized.
Integrated network and host-based intrusion detection and response systems can be provided by
Open Technology. This maximum level of around-the-clock surveillance extends unobtrusively across the enterprise, allowing administrators to automatically monitor network traffic and host logs, detect and respond to suspicious activity, and intercept and respond to internal or external host and network abuse before systems are compromised.
Nowadays, a company's network environment supports more users and critical applications, and has more dependency on the Internet. The technologies drives business today ie. laptops and other mobile networking devices, e-mail, WiFi and other unsecured Internet connection. Technologies are creating security vulnerabilities that can leave a business open to significant losses in information, revenue and equipment. Even though security solutions are improving, the attack technologies are in near- lockstep with those gains.
The ultimate goal for an enterprise is to protect WAN and LAN endpoints and to maintain a safe productivity level that results in improving business results while reducing costs and losses due to security incidents.
Open Technology can provide an effective security approach goes beyond simply applying the technology to address the process itself, as well as the people using and managing it. The overall solution is to manage security as a process that works from the inside out.
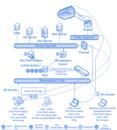
The NAC (Network Admission Control) market has been a bunch of hot air. While the big vendors focus on the demands of admission control, the market really needs post-connect controls for privileged activity, threat reduction, and compliance management.
The discipline of network access control (NAC) of knowing and controlling who and what is connecting to your network at all times has emerged as a basic business requirement. It reduces the risk of rogue, guest, infected, or otherwise non-compliant systems compromising your network, and lets you know precisely when your network is at risk.
Network Access Control (NAC) technology promises to dramatically reduce both the number and severity of security events as well as aid in regulatory compliance. But there's uncertainty about the direction that NAC standards will take, which is why some enterprises have been reluctant to deploy a NAC solution.
What are the main problems we hope to solve via a NAC solution?
- Stemming the tide of worms and viruses that proliferate in the network.
- Securing corporate information by protecting our endpoints.
- Ensuring the return on investment of prior security applications making sure they are all being used properly by all my users.
- Stopping rogue/unauthorized use of my network and mitigating the risk it imposes.
- Meeting internal or external regulations.
- Managing guest access to the network.
- Ensuring that my patch operation system is operating correctly and necessary patches are installed on all my machines.
- Ensuring that every user on the network is identified.
- Protecting the enterprise by ensuring no file sharing or peer-to-peer applications are operating on connected endpoints.
What access methods do we need to control?
- Remote via VPN
- LAN via wired connections
- LAN via wireless connections
NAC is a software solution that works with an organizations current networks to control access of all users based on who they are, where they are accessing the network, and the security state of their computer as dictated by the organizations policies. By supporting current network hardware and all security applications, using standards to prepare for tomorrows networks, and providing a solution that is scalable and configurable to meet specific business needs.
Open Technology understands that NAC is about much more than admission control and can provide the best services in the market.
Service provider must be responsible for IT society in concept of IT Governance which is nowadays very famous and related to regulation of the wrong act of computer in case of there is a situation of wrong act of computer which authorized person have to investigate and find information which in form of digital format file.
It is kept in system or Log file which gains from activities in system. It is called Traffic Data in law system which is specified by law to keep as much as necessary which means it does not need to keep every Traffic Data occurred in system (it is impossible in practical), for example, it must store only Source IP address, Destination IP address, Date, Time and User Name (if there is).
This is for staff s can prove any evidence by means Computer Forensic and can backward investigate in maximum 1 year, in case of occurred situation which there is more than 90 days is important to become responsible of every organization especially service providers are needed to cooperate to meet real objective of this law.
Information storage of network system
- Fundamental network system must store needed information for staff, such as, source, origin, destination, time, date, quantity, timing of service type or others which relate to connection of computer system.
- Fundamental network system must store information from 90 days to 1 year.
- Fundamental network system must identify user in system whether who or normal system or wireless system.
Summary
- The important operation for efficiency network system development to support regulation.
Process:
- Authentication system to identify the right user.
- Create time standard system by setting NTP Server and set every equipments to adjust accurate time.
- Set Centralized Log Server system which can storage information for 90 days.
- Prevent user in system not to harm other network system.
Policy : how to help user have clearly performing way
People : how to create safety conscious for user